
Découvrez en quoi l’eSIM est plus avantageuse que la carte SIM traditionnelle en termes de fonctionnalités, coûts et praticité pour 2026.

Toutes les ressources pour maîtriser vos connexions mobiles : guides, comparatifs et astuces de sécurité.

Découvrez en quoi l’eSIM est plus avantageuse que la carte SIM traditionnelle en termes de fonctionnalités, coûts et praticité pour 2026.


Découvrez comment scanner un QR code pour configurer facilement votre eSIM et profiter rapidement de votre forfait mobile en 2026.


Découvrez notre avis détaillé sur la carte eSIM Truphone en 2026 avec des retours d'expérience fiables pour choisir le meilleur service mobile.


Découvrez comment utiliser une eSIM pour avoir une connexion mobile fiable dans le monde entier lors de vos voyages en 2026 et restez connecté facilement.


Découvrez comment la vitesse internet avec une eSIM peut être optimisée en 2026 pour profiter d'une connexion rapide et stable sur tous vos appareils.

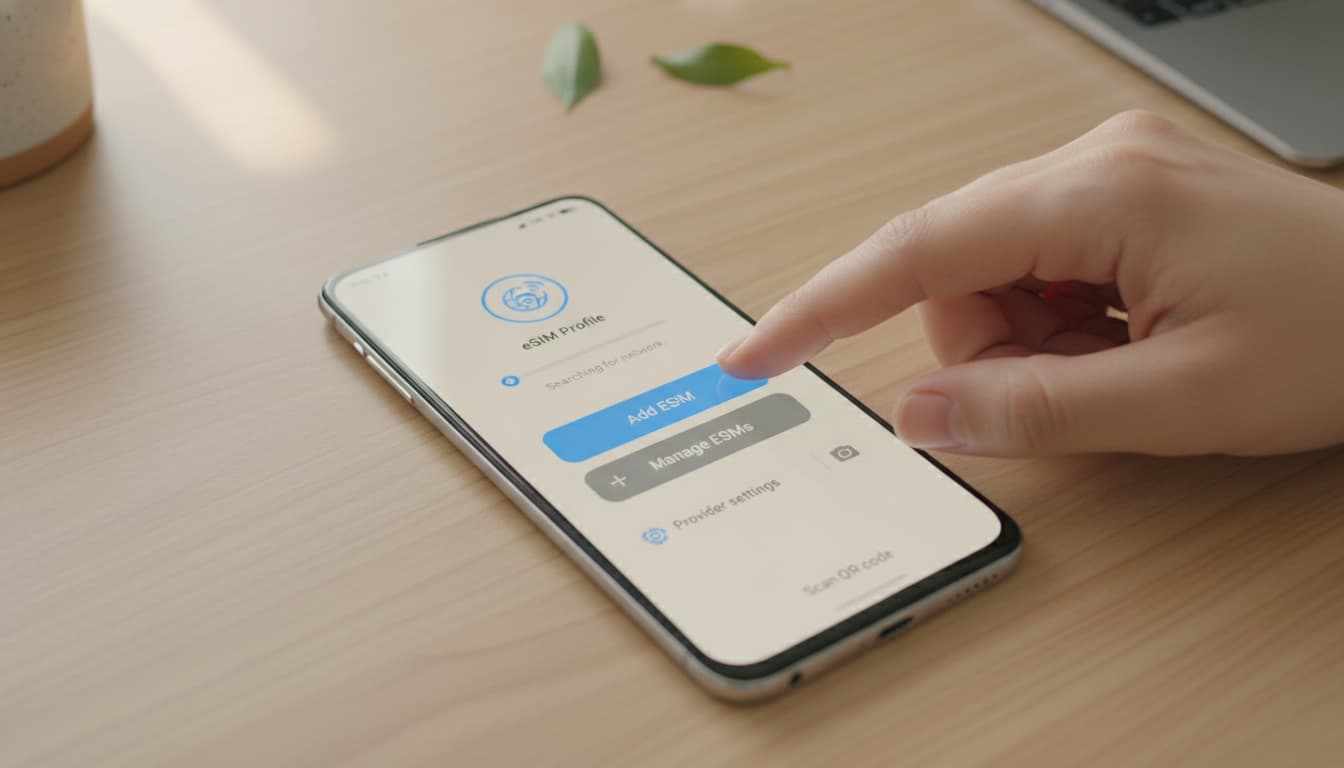
Découvrez comment installer et configurer facilement une eSIM sur votre smartphone Xiaomi en 2026 grâce à ce guide détaillé et pratique.

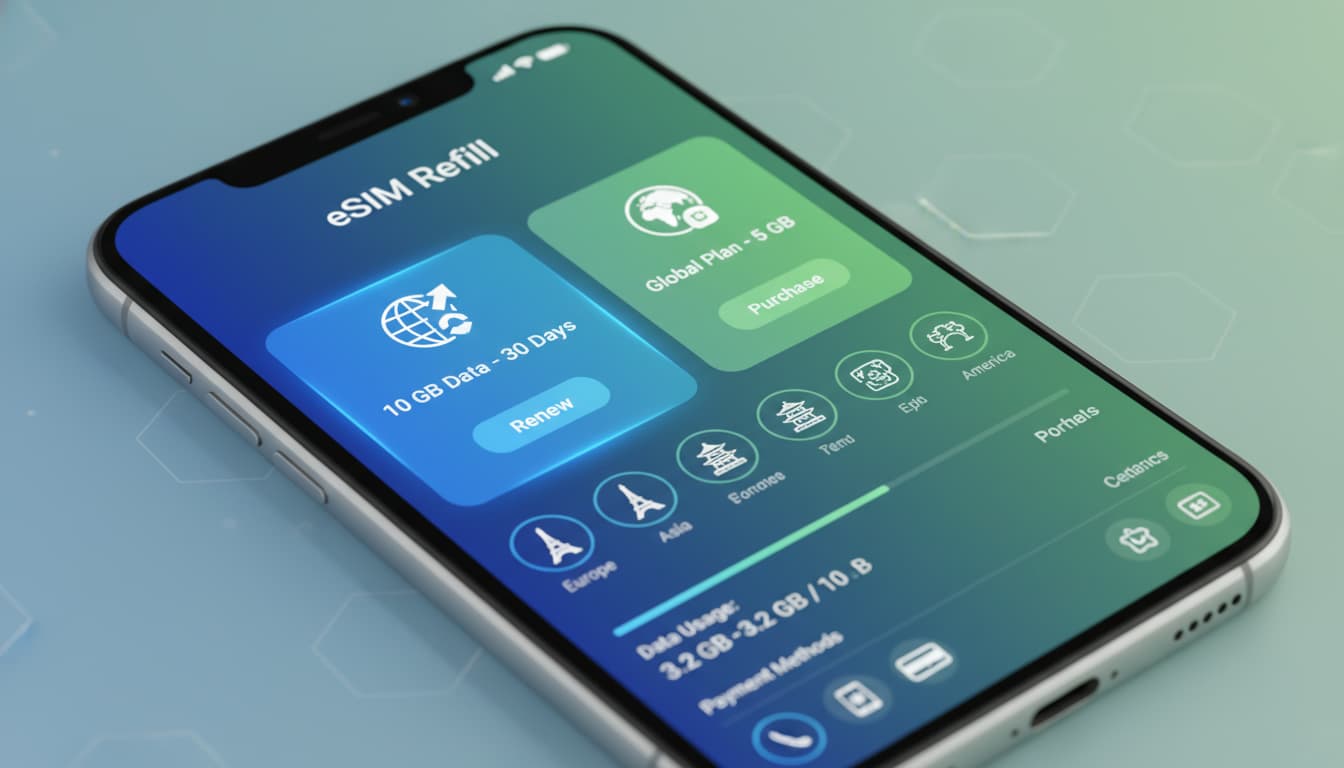
Découvrez comment ajouter ou renouveler un forfait de données sur votre eSIM en 2026 pour rester connecté sans interruption.


Découvrez comment acheter, activer et utiliser une eSIM pour votre voyage au Canada en 2026. Profitez d’une connexion facile et rapide dès votre arrivée.


Découvrez comment identifier et régler un problème réseau eSIM sur votre appareil en 2026 pour profiter d'une connexion stable et rapide facilement.

Découvrez les options, fournisseurs et avantages d’une eSIM pour l’Amérique du Sud en 2026 et profitez d’une connexion facile et flexible.


Découvrez les avis sur la carte eSIM 1Global pour évaluer sa qualité, ses fonctionnalités et sa fiabilité avant de l’acheter en 2026.

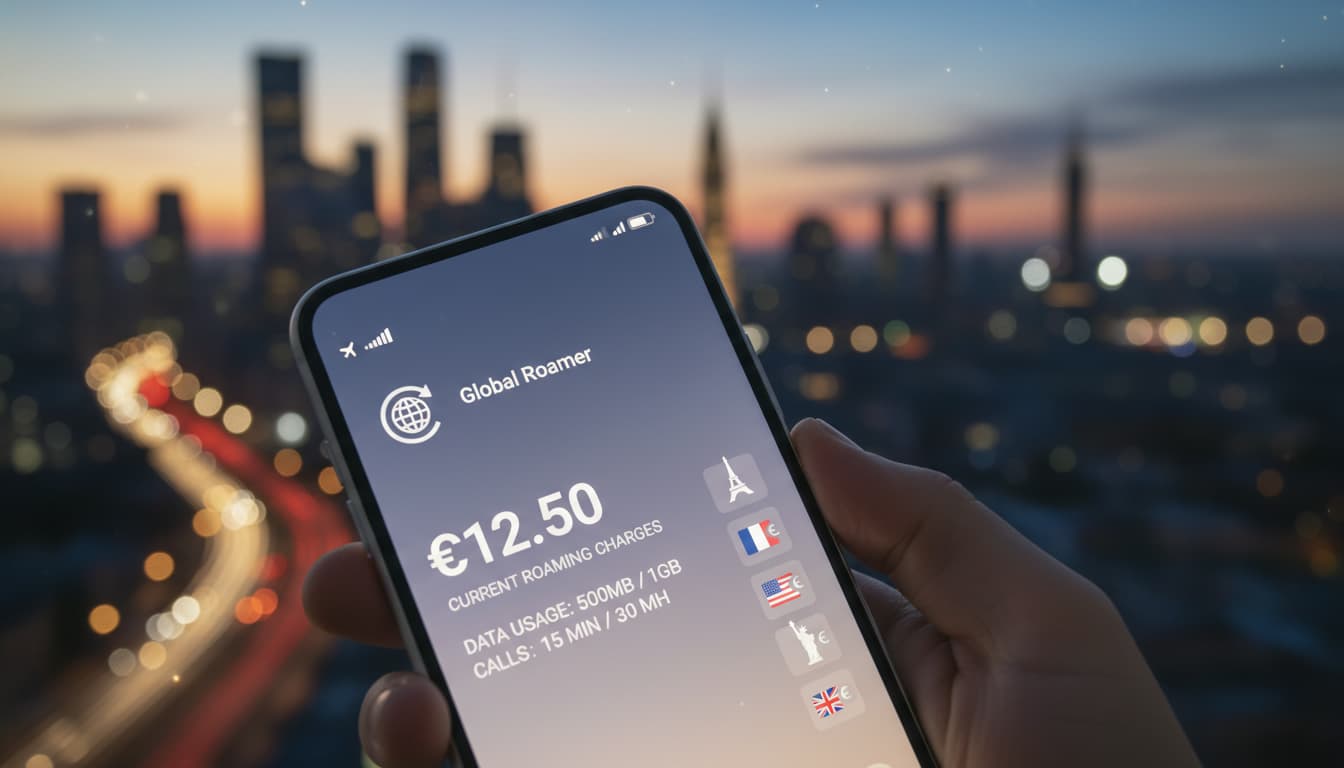
Découvrez les coûts liés à l’utilisation d’une eSIM en roaming à l’étranger et évitez les surprises grâce à nos conseils pratiques pour 2026.
